Basics of Cryptography - Part 1
Applied Cryptography In Simple Words - Part 1
In this Article, we are going to review basic terminologies and concepts of Cryptography. In next Parts we will explain practical implementations of the following subjects which are covered in this Article:
Next parts of this Blog will cover actual implementation/use cases of the followings:
- Basic Terms & Definitions in Cryptography
- Trapdoor function & One Way Hash function concepts and use cases
- Symmetric/Asymmetric Encryption & Digital Signatures
- Part 2: Encrypt Files & transfer both Files and Keys to Recipient (OpenSSL).
- Part 3: Mutual Certificate - mTLS use case (Certificates,Symmetric&Asymmetric).
- Part 4: Consumer to Service Authenticity verification & Access controls using JWS.
Basic Terms & Definitions in Cryptography
 |
| Cryptography Terminologies |
- Plaintext: Readable content. not protected contents, sender sends to the receiver on communication channels.
- Ciphertext: Mutated Plaintext which is scrambled and mathematically very difficult to revert back. Can not be understood by potential Interceptors in the middle of way.
- Key: Critical value/values fed in to algorithms to mutate Plaintext in to Ciphertext and/or revert Ciphertext back to Plaintext.
- Encrypt: The mechanism through which a Key is used to convert the Plaintext in to Ciphertext via specific algorithm.
- Decrypt: The mechanism through which a Key is used to convert Ciphertext back to Plaintext via specific algorithm.
- Trapdoor functions: A trapdoor function is a function that is easy to perform in one way(encrypt D->R with `t`), but there is a need for the (`t`) with out which the other way; inverse calculation is a big challenge & computationally expensive. This is a classic concept used by any Encryption/Decryption mechanism.
 |
| Keyed Hash Functions; HMAC |
- One way hash functions: A function which takes an input/message and returns a fixed-size output value accordingly. The output of a hash function is called 'hash value', 'message digest', 'digital fingerprint', 'digest' or 'checksum'. A pure Hash function (with no Salt or same Salt) will generate same output for the same input value. As the outputs suggest it can be used for integrity checks to make sure if a message has been preserved and not modified unexpectedly while on flight. Additionally hash functions could be used as data level controls use as a Tokenization method within privacy domains. This means not the actual values but only digests can be transferred, processed and stored. There are no keys involved to revert the calculations, yet there are possible attacks against hash functions to derive back or indirectly infer the actual data through some computation efforts. Hash functions used with Salt and sometime Peper provide more robustness against such attacks by increasing the expensiveness of that computation effort. Additionally there are certain usage of Hash functions with keys as message authentication codes (HMAC). HMACS are used for Authenticity verification when used as digital signature. They are not only used for integrity check but also help to make sure the received message is sent only by the party who knows the Key to the hash function in advance. Example: AWS Signature Version 4. Please note in HMAC the Key is used to derive back the Actual Hash functions and not the original hashed values.
2 Main Types of Encryption/Decryption mechanism; Symmetric vs Asymmetric
Each mechanism may include different algorithms with varieties of trapdoor & hash functions. The important thing to note is that algorithms could be openly known to everyone. For usage and implementations of such mechanism the secrecy of the algorithms should not be relied on. Obscurity does not equal Security.
Cryptography Rule of Thumb
Security of such mechanisms relies on correct implementations and the only elements that should be preserved (kept secret) are Secrets/ Private Keys which are the main jewels. There are rigid industry standards on cryptographic modules and on how to handle Secrets (such as FIPS-140-2 & FIPS-140-3) . Handle in this case means: generate,manage,store, use, rotate(change) & dispose. In this regard, let's quote Auguste Kerckhoff's desideratum and & Shannon's maxim principle of cryptography which clearly suggests Security can never be achieved by Obscurity:
Cryptography Rule of Thumb
Security of such mechanisms relies on correct implementations and the only elements that should be preserved (kept secret) are Secrets/ Private Keys which are the main jewels. There are rigid industry standards on cryptographic modules and on how to handle Secrets (such as FIPS-140-2 & FIPS-140-3) . Handle in this case means: generate,manage,store, use, rotate(change) & dispose. In this regard, let's quote Auguste Kerckhoff's desideratum and & Shannon's maxim principle of cryptography which clearly suggests Security can never be achieved by Obscurity:
- Kerchoff: "A cryptosystem should be secure even if everything about the system, except the key, is public knowledge."
- Shannon: "The enemy knows the system"
plaint text and transform it to cipher text is same as the key used to decrypt cipher text and transform it back to plain text. Lets assume an analogous example of the key to your house. You may make copies of it and give copies to a friend or maintenance contractors. How do you transfer the key in advance? perhaps you send it by Post? what if some one make a copy of it while it is being transferred ? Now time to worry right? Even if the transfer is secure How frequently do you change lock and make new Keys? That is why Key/Secret rotation is necessary. If you never change the Lock/Keys what happens?
Examples: AES, Blowfish, RC4-5-6
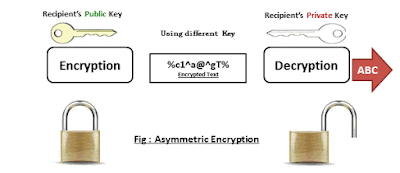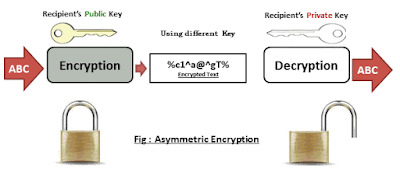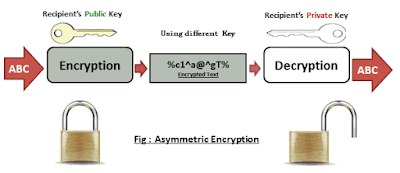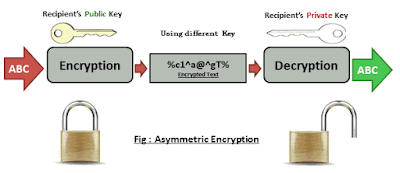
2.Asymmetric: There are two keys. A 'Key Pair' exists (private & public). One is meant to be your `Secret`, the other is meant to be shared `Public`. You never share the `Secret` with any one. Others can use the `Public` one to encrypt. Who ever has access to the paired 'Secret' can decrypt. hence, unlike symmetric, encryption and decryption keys are not the same here. One is used for encryption the other is used for decryption. In the use case of Digital Signatures the Keys are used vice versa, exactly the other way. The Private Key is used to sign/encrypt a hashed message and sent to the receiver who upon receipt verify the signature by decrypting the message with the Public Key. If conversion happens successful authenticity of the sender could be verified, why? because only the sender is the only one who is supposed to have the private key.
 |
| Asymetric Digital Signature |
In Practice mix of both Symmetric & Asymmetric mechanisms are widely used to provide Confidentiality, Integrity and Authenticity. When browsing website in HTTPS format both Symmetric & Asymmetric Cryptography are relied during TLS record & Handshakes to provide:
- Authenticity Verification (via Digital Certification & Signature)
- Confidentiality (via Encryption)



Comments
Post a Comment